Career-Aligned Cybersecurity Training, Powered by IronCircle
Accelerated Learning | Hands-On Practice | Real-World Simulations

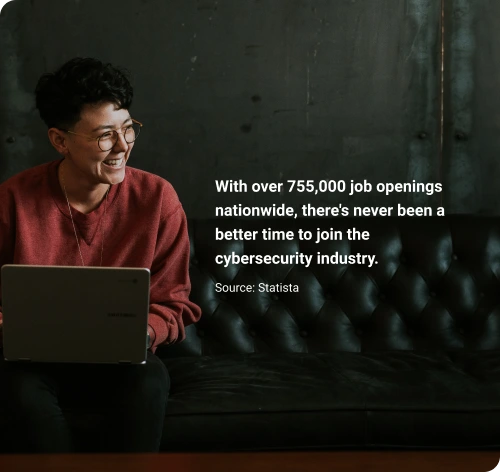
Outsmart the Competition and Excel in Your Career
Learn on an Industry-Leading Platform
The Cyber Defense Track + Certified Cybersecurity Associate is designed to kickstart your cybersecurity career, no matter your current level of tech knowledge. Go from beginner to job-ready professional with AI-powered, expert-developed training.
You start with cybersecurity fundamentals and progress through more advanced tasks, preparing you for real-world challenges you’ll experience on the job.
The Cybersecurity Bootcamp is offered through the Continuing Education services of Penn State Beaver and Penn State Behrend.
Become a Cyber Defender With Hands-On Training
Hands-On Courses
Engage in practical exercises and simulations to develop the job-ready skills needed to succeed in the cybersecurity field.
Personalized Learning
Gain context-aware guidance and customized learning from a platform that adapts to your strengths and weaknesses.
Applied Certifications
Demonstrate and prove real skills through practical, role-based, scenario-driven assessments.
Browser-Based Platform
Study online, on your own schedule, in your web browser. No setup necessary.

Discover Everything You’ll Learn
Read the program guide.
Program Overview
Cyber Defense Track + Certified Cybersecurity Associate
- Certified Cybersecurity Associate
Certified Cybersecurity Associate introduces you to the foundational skills and tools of cybersecurity through a hands-on, applied approach. As you begin your cyber career journey, this entry-level certification prepares you for real roles in just 100 hours of flexible, online learning.
- Certified Cybersecurity Analyst
Certified Cybersecurity Analyst is a hands-on, technical certification that prepares you for entry-level roles in Security Operations Centers (SOCs). Through three stackable micro-credentials, you’ll gain practical experience in log analysis, SIEM tools like Splunk, incident escalation, and SOC communication.
- Certified SOC Analyst
Certified SOC Analyst prepares you for entry-level SOC roles. In IronCircle’s real-world labs and blue team scenarios, you’ll build practical skills in log analysis, threat detection, alert triage, and incident response, all mapped to the workflows used in modern SOC environments.
- Certified CTI Analyst
Certified CTI Analyst trains you to collect, analyze, and operationalize cyber threat intelligence to strengthen real-world defense efforts. Use structured analysis techniques and real-world threat hunting scenarios to learn to track threat actors, uncover malicious infrastructure, and deliver actionable insights that improve security decision-making.

Pricing
Invest in yourself and your professional growth. Get started today and advance your cybersecurity career.
$14,490*
Cyber Defense Track + Certified Cybersecurity Associate
Requirements
-Internet access
-Commitment to your career goals—no tech background necessary
*Price reflects the Bundle & Save Discount available from IronCircle partners. Program MSRP is $19,000. Pricing and fees are subject to change.
