Cybersecurity Bootcamp, Powered by ThriveDX
Accelerated Program | Online Classes

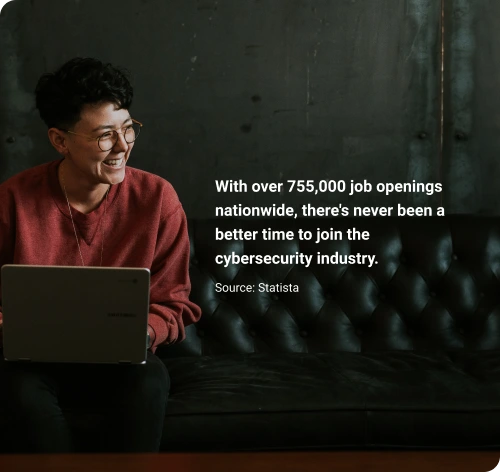
Outsmart the Competition and Excel in Your Career
Comprehensive, Hands-on, Virtual Education
This non-credit, non-degree program is built for those looking to fast-track their career in cybersecurity, whatever their initial level of tech proficiency. Expert instructors guide your training in a safe cloud-based platform where you can practice defending and attacking various systems and applications. You will complete the program ready to defend organizations against real attacks, find weaknesses, and secure systems from threats–all the skills employers look for.
Additionally, our courses are regularly updated to incorporate the latest advancements in cyber tech, including AI tools and practices.
The Cybersecurity Bootcamp is offered through the Continuing Education services of Penn State Beaver and Penn State Behrend.
Train on the Industry’s Top Tools and Software
Develop the advanced skills and training you’ll need to become a well-rounded cybersecurity professional, covering everything from the basics to advanced industry skills.

Learn to Defend Against Cyberattacks
Hands-On Learning
Confidently enter the workforce with hands-on training in an accelerated, online environment. Gain real-world experience designed for professionals of all backgrounds and experience levels to excel in the field of cybersecurity.
Virtual Classroom
Top-tier instructional methodologies are used with cloud-based chat software that encourages real-time interaction between you and your instructors. Attend classes virtually from the comfort of your own home on weekday evenings.
Industry-Leading Instructors
Learn from expert instructors with current industry knowledge and a unique insider’s understanding of the fast-paced field of cybersecurity. Access guidance from thought leaders as you learn how to succeed as a cybersecurity professional.
TDX Arena
Gain experience through real-world simulations identifying vulnerabilities on web, server, mobile, and desktop platforms and learn how to protect against cyber threats with our proprietary virtual platform, TDX Arena.
Personalized Support Every Step of the Way
Networking Advantages
Attend virtual networking events, including career fairs, industry panels, mock interview days, skill-building webinars, and more.
Career Coaching
Access a team of career coaches eager to help you achieve your professional goals in your cybersecurity career. Professional development is available to assist in resume writing, LinkedIn profile building, interview prep, and beyond.
Learner Support
Your journey into the field of cybersecurity is backed by a dedicated team. Your Learner Services Manager will help ensure you have the tools and support you need to succeed throughout the program.
Job Search Assistance
Our Learner Services team will assist in your search to find exciting job opportunities. Prepare for the interview process with our professional assistance to start your new career with confidence.

Download the Course Catalog
Find out what you will learn.
Program Overview
32-Week Complete Program
- Fundamentals Phase12 Weeks
The Fundamentals Phase covers essential cybersecurity principles, including network basics and their functions, Microsoft’s infrastructure, and Linux operating system management.
By completing this phase, you will establish a solid foundation and gain a comprehensive understanding of fundamental cybersecurity concepts.
- Computer Networking Fundamentals
This course offers a comprehensive introduction to computer networking, providing practical experience in configuring and managing network devices for optimal performance and security. Learners will gain an understanding of network architectures, protocols, and security while honing their device configuration and troubleshooting skills. Through hands-on activities, they will apply critical thinking and problem-solving skills to address common networking challenges.
Learners will:
- Learn how different entities connect and interact across digital landscapes.
- Gain an understanding of the various types of networks and their impact on our interconnected world.
- Harness the power of configuration settings documentation.
- Be exposed to the role of audits in ensuring optimal network performance and security.
- Find out why system and communications protection plays a pivotal role in safeguarding information.
- Learn how to effectively update and adapt policies to keep pace with the ever-evolving landscape.
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® Network+, ISC2 Certified in Cybersecurity℠
- Microsoft Security Systems Administration
This course offers hands-on training focused on securing Microsoft Windows environments, providing learners with the practical knowledge and skills needed to implement security features and tools, including Microsoft Defender, BitLocker, and Windows Firewall. They will also be able to configure and manage networks to ensure security and stability using system admin tools. By the end of the course, participants will understand the basics of Microsoft infrastructure and be able to implement and maintain secure Windows environments in various professional roles.
Learners will:
- Gain an understanding of Microsoft infrastructure and its components.
- Learn effective strategies to protect Microsoft’s infrastructure from potential threats.
- Develop skills to manage various types of accounts based on business function.
- Explore ways to maintain a secure and safe network environment.
- Discover how automations and scripting can enhance both security and efficiency in cybersecurity roles.
- Understand how Active Directory helps manage permissions and control access to network resources.
- Learn how to improve system security and operational efficiencies with Powershell.
- Integrating Your Infrastructure Security
This course equips learners with the necessary skills to manage Linux operating systems, utilize basic Python programming, explore cloud computing, and enhance system security against threats and vulnerabilities. Additionally, they will learn how to monitor, scan, and analyze threats and vulnerabilities in these environments, while also becoming familiar with remediation techniques. Finally, learners will begin to understand how DevSecOps impacts the cybersecurity landscape.
Learners will:
- Gain an understanding of how to manage Linux operating systems, as well as how to monitor, scan, and analyze threats and vulnerabilities in Linux and cloud-based environments.
- Be introduced to Python programming.
- Develop a basic understanding of cloud computing environments and create an instance using Amazon Web Services (AWS).
- Understand how to remediate and share details to protect other systems.
- Learn how to create automations to efficiently manage and protect systems.
- Explore the design principles of scalable cloud solutions and the integration of different environments.
- Become familiar with DevSecOps.
Information covered in this course helps prepare learners to begin studying for the following certification:* AWS Cloud Practitioner
- Infrastructure Phase12 Weeks
The Infrastructure Phase provides learners with the essential knowledge and practical experience to establish and maintain secure infrastructures and technologies. Gain practical skills in applying critical security measures, as well as an understanding of a hacker’s perspective, to safeguard organizational systems.
- Securing Your Network
In this course, you continue building on your knowledge of networks to deepen that understanding. As you explore networks, you will familiarize yourself with the different components of wired and wireless networks including their security constraints and vulnerabilities. You will then continue to develop access controls to ensure that you have considered what it means to secure a network from people and data to devices. In addition, you will look at how to safely build and secure networks including discussions around cryptography and privacy constraints.
Learners will:
- Develop an understanding of network security measures, including strategies needed to keep networks safe.
- Begin to master network monitoring techniques.
- Gain an understanding of how to manage accounts within a system effectively.
- See how security attributes can help strengthen network defenses.
- Become familiar with a range of common tools and technologies that support network safety.
- Acquire the skills to build a secure network architecture.
- Learn the basics of MHN networks and how to set them up effectively.
- Understand the relationship between Telnet and POP3 machines.
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® Network+, Cisco Certified CyberOps Associate
- Designing Your Cybersecurity Infrastructure
This course delves into the essential aspects of safeguarding endpoint devices, implementing data loss prevention techniques, and utilizing advanced tools and strategies to protect an organization’s digital assets. By the end of the course, participants will have a comprehensive understanding of endpoint device protection, data loss prevention, and security considerations for industrial systems and IoT devices.
Learners will:
- Explore endpoint devices to gain an understanding of how to evaluate, identify threats to, and protect them.
- Learn to document and track configurations and tool options.
- Understand how to establish rules and restrictions that safeguard endpoint devices from potential harm.
- Discover how to work with external information systems while maintaining the security of endpoint devices.
- Develop the skills to implement data loss prevention techniques.
- Become familiar with the threats and security measures related to Industrial Control Systems (ICS) and Industrial Internet of Things (IIOT).
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® Security+, CompTIA® CySA+, ISC2 CISSP
- Social Engineering and Ethical Hacking
In the Social Engineering and Ethical Hacking course, participants explore the inner workings of hackers’ minds and acquire an understanding of game theory principles as they relate to cybersecurity defense and solutions. By the end of the course, learners will have an understanding of social engineering techniques and ethical hacking principles, empowering them to enhance cybersecurity defenses and protect against potential threats.
Learners will:
- Gain insights into the motivations of potential attackers and their actions.
- Develop an understanding of how to use a malicious hacker’s “state of mind” to enhance system protection.
- Discover how ethical hacking can proactively support applications, systems, and organizational infrastructure.
- Explore how reconnaissance, penetration testing, and defense system bypassing can help keep systems safe.
- Learn how to identify vulnerabilities in web applications and cloud-based systems
- Build skills to effectively report risks and provide defense recommendations.
- Understand how social engineering techniques can be used to deceive individuals.
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® CySA+, PenTest+
- Advanced Phase8 Weeks
The Advanced Phase equips you with the knowledge and tools to respond to attacks and secure systems against future threats using digital forensics and post-attack response tools.
Upon successful completion of this phase, you will receive your Cybersecurity Bootcamp Certificate of Completion.
- Digital Forensics and Incident Response
This course equips learners with essential tools to effectively respond to attacks, conduct investigations, gather evidence, and produce comprehensive reports. By the end of the course, participants will have the necessary knowledge to respond to incidents, run investigations, and report their findings. These skills will help students to recognize, analyze, and ideate about security incidents to prevent future breaches.
Learners will:
- Be immersed in the fundamentals of offensive security.
- Gain an understanding of the basics of digital forensics.
- Explore file and stolen data recovery strategies.
- Learn how to effectively handle various types of attacks targeting organizations.
- Get insight into the strategies attackers use to attain access to critical systems and data.
- Explore the basics of malware analysis to enhance your ability to detect and neutralize potential threats.
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® Security+, CompTIA® CySA+, and ISC2 SSCP
- Threat Hunting and Intelligence
The Threat Hunting and Intelligence course provides learners with the knowledge to identify and mitigate vulnerabilities in an organization’s infrastructure. By the end of the course, learners will be equipped with the expertise to identify vulnerabilities, respond to threats, and develop robust plans to safeguard an organization’s infrastructure.
Learners will:
- Develop a comprehensive understanding of the threats and vulnerabilities that can arise within an organization’s network infrastructure, encompassing hardware devices, software applications, and network services.
- Enhance their ability to proactively identify and respond to threats, fostering a proactive security approach.
- Acquire the knowledge and skills to develop effective plans and procedures to handle security situations efficiently, ensuring a swift and coordinated response.
- Cultivate the ability to evaluate information sources and tools, enabling them to strengthen their defense strategies.
Information covered in this course helps prepare learners to begin studying for the following certifications:* CompTIA® Security+, CompTIA® CySA+, ISC2 SSCP, ISC2 CISSP
*For more information, please visit thrivedx.com/cybersecurity-program-disclaimers.
Gear Up for Internationally Recognized Certification Exams
This bootcamp is not a certification-prep program. However, we recognize that cybersecurity professionals breaking into the industry are more likely to be hired if they hold internationally recognized certifications. In an effort to boost your credentials even further, we have incorporated foundational information in our curriculum to help you develop skills applicable to certification exams.*
AWS Certified Cloud Practitioner
The AWS Certified Cloud Practitioner certification exam is meant for individuals with knowledge of the widespread AWS Cloud platform, as well as its infrastructure and systems. Security and compliance experience in AWS Cloud is a key requirement for passing the exam.
The Cybersecurity Bootcamp includes complimentary access to the AWS Academy curriculum and a discounted voucher for the AWS Certification exam.* Program materials help provide a real-world understanding of AWS Cloud practices so learners can pursue AWS Cloud Certification to work in entry-level roles.
*For more information, please visit https://thrivedx.com/cybersecurity-program-disclaimers.
Certified Information Security Manager
Data breaches, ransomware attacks, and other constantly evolving security threats are top-of-mind for today’s IT professionals. With a Certified Information Security Manager® (CISM®) certification, you’ll learn how to assess risks, implement effective governance, and proactively respond to incidents.
CertNexus® CyberSec First Responder® (CFR)
The Cybersecurity Bootcamp helps learners prepare for the CertNexus® CyberSec First Responder® (CFR) certification. A 20% discount for CertNexus® certifications and prep material is available to learners upon completion of the program.*
*For more information, please visit https://thrivedx.com/cybersecurity-program-disclaimers.
Cisco Certified CyberOps Associate
The Cisco Certified CyberOps Associate certification allows learners to gain an understanding of how Security Operations Centre (SOC) teams detect and respond to security incidents and is considered a great starting point for cybersecurity professionals.
CompTIA® CySA+
Designed to provide a higher focus at an intermediate level on applying behavioral analytics to networks than the CompTIA® Security+ exam, this exam will cover core cybersecurity skills while placing a greater significance on software and application security. Additionally, it will cover automation, threat hunting, and IT compliance within the industry.
CompTIA® Network+
The CompTIA® Network+ certification exam measures a learner’s ability and knowledge of network device configuration, management, and troubleshooting. It also tests a cybersecurity professional’s familiarity with emerging mobile, cloud, communication, and virtualization technologies.
CompTIA® Security+
The CompTIA® Security+ certification is a globally recognized credential that validates foundational skills in cybersecurity, including threat management, risk assessment, and network security. It’s ideal for entry-level security professionals and is often a key stepping stone for careers in information security and IT.
GIAC Certified Incident Handler
The GIAC Incident Handler certification validates a practitioner’s ability to detect, respond, and resolve computer security incidents using a wide range of essential security skills. GCIH certification holders have the knowledge needed to manage security incidents by understanding common attack techniques, vectors, and tools, as well as defend against and respond to such attacks when they occur.
GIAC Security Essentials
The GIAC Security Essentials (GSEC) certification validates a practitioner’s knowledge of information security beyond simple terminology and concepts. GSEC certification holders are demonstrating that they are qualified for hands-on IT systems roles with respect to security tasks.
ISC2 SSCP – Systems Security Certified Practitioner
Learners with at least one year of experience after the completion of their program can take the ISC2 SSCP – Systems Security Certified Practitioner certification exam.*
The ISC2 SSCP exam is meant for cybersecurity professionals who have proven, practical, and hands-on experience and knowledge of the security environment. Once they obtain this certification, individuals have proof that they can carry out the implementation, monitoring, and administration of information technology infrastructure according to information security best practices, policies, and procedures.
*Requires a minimum of one year of cumulative work experience in one or more of the seven domains of the SSCP Common Body of Knowledge (CBK) in order to be certified.
LPI Linux Essentials
The Linux LPI Essentials exam offers learners a way to verify their knowledge of the Linux operating system, as well as the workings of various open-source applications. The exam tests the ability to manage users and groups on Linux and also measures their competency with the Linux command line, system permissions and security, basic network configuration skills, and overall Linux administration.
- AWS Certified Cloud Practitioner
The AWS Certified Cloud Practitioner certification exam is meant for individuals with knowledge of the widespread AWS Cloud platform, as well as its infrastructure and systems. Security and compliance experience in AWS Cloud is a key requirement for passing the exam.
The Cybersecurity Bootcamp includes complimentary access to the AWS Academy curriculum and a discounted voucher for the AWS Certification exam.* Program materials help provide a real-world understanding of AWS Cloud practices so learners can pursue AWS Cloud Certification to work in entry-level roles.
*For more information, please visit https://thrivedx.com/cybersecurity-program-disclaimers.
- Certified Information Security Manager (CISM)
Data breaches, ransomware attacks, and other constantly evolving security threats are top-of-mind for today’s IT professionals. With a Certified Information Security Manager® (CISM®) certification, you’ll learn how to assess risks, implement effective governance, and proactively respond to incidents.
- CertNexus® CyberSec First Responder® (CFR)
The Cybersecurity Bootcamp helps learners prepare for the CertNexus® CyberSec First Responder® (CFR) certification. A 20% discount for CertNexus® certifications and prep material is available to learners upon completion of the program.*
*For more information, please visit https://thrivedx.com/cybersecurity-program-disclaimers.
- Cisco Certified CyberOps Associate
The Cisco Certified CyberOps Associate certification allows learners to gain an understanding of how Security Operations Centre (SOC) teams detect and respond to security incidents and is considered a great starting point for cybersecurity professionals.
- CompTIA® CySA+
Designed to provide a higher focus at an intermediate level on applying behavioral analytics to networks than the CompTIA® Security+ exam, this exam will cover core cybersecurity skills while placing a greater significance on software and application security. Additionally, it will cover automation, threat hunting, and IT compliance within the industry.
- CompTIA® Network+
The CompTIA® Network+ certification exam measures a learner’s ability and knowledge of network device configuration, management, and troubleshooting. It also tests a cybersecurity professional’s familiarity with emerging mobile, cloud, communication, and virtualization technologies.
- CompTIA Security+
The CompTIA® Security+ certification is a globally recognized credential that validates foundational skills in cybersecurity, including threat management, risk assessment, and network security. It’s ideal for entry-level security professionals and is often a key stepping stone for careers in information security and IT.
- GIAC Certified Incident Handler (GCIH)
The GIAC Incident Handler certification validates a practitioner’s ability to detect, respond, and resolve computer security incidents using a wide range of essential security skills. GCIH certification holders have the knowledge needed to manage security incidents by understanding common attack techniques, vectors, and tools, as well as defend against and respond to such attacks when they occur.
- GIAC Security Essentials
The GIAC Security Essentials (GSEC) certification validates a practitioner’s knowledge of information security beyond simple terminology and concepts. GSEC certification holders are demonstrating that they are qualified for hands-on IT systems roles with respect to security tasks.
- ISC2 SSCP – Systems Security Certified Practitioner
Learners with at least one year of experience after the completion of their program can take the ISC2 SSCP – Systems Security Certified Practitioner certification exam.*
The ISC2 SSCP exam is meant for cybersecurity professionals who have proven, practical, and hands-on experience and knowledge of the security environment. Once they obtain this certification, individuals have proof that they can carry out the implementation, monitoring, and administration of information technology infrastructure according to information security best practices, policies, and procedures.
*Requires a minimum of one year of cumulative work experience in one or more of the seven domains of the SSCP Common Body of Knowledge (CBK) in order to be certified.
- LPI Linux Essentials
The Linux LPI Essentials exam offers learners a way to verify their knowledge of the Linux operating system, as well as the workings of various open-source applications. The exam tests the ability to manage users and groups on Linux and also measures their competency with the Linux command line, system permissions and security, basic network configuration skills, and overall Linux administration.
*For more information, please visit https://thrivedx.com/cybersecurity-program-disclaimers

Program Tuition
Now is the time to seize this opportunity to enter a new career in the tech field. Invest in your professional development with the knowledge and skills you need to enter the field of cybersecurity.
$18,900*
32-Week Cybersecurity Bootcamp
Requirements
- Internet access
-$50 registration fee*
*Tuition, fees, and deposits are subject to change. Registration fee is non-refundable.






